Safeguarding your data against cyber threats is essential in today’s digital landscape. At DornerWorks, we offer comprehensive cybersecurity solutions to bring confidence to your organization’s cybersecurity plan and product development.
With the exponential growth of global data and the relentless pursuit of valuable information by sophisticated hackers and nation states, safeguarding your data has never been more critical.
We understand what you’re up against, which is why we offer comprehensive solutions to fortify your organization against potential breaches.

Our compliance standards, including AS9100, ISO 13485, ITAR registration, NIST 800-171, NIST 800-53, FDA Standards in Cybersecurity, and CMMC Level 2, ensure that our network follows industry best practices and remains secure. We’re committed to helping you implement stronger cybersecurity measures in your products and organization.
Get a comprehensive overview of our security niches and strategies here, and explore the following valuable resources to learn more about implementing or enhancing a robust cybersecurity plan.
Stay informed with our podcast series that dives deep into cybersecurity topics.
Gain insights from our expert team on medical software security, protecting against data breaches, building secure IoT devices, and more.
Access essential guidance documents, articles on postmarket cybersecurity, incident reports, Software Bill of Materials (SBOM) and more:
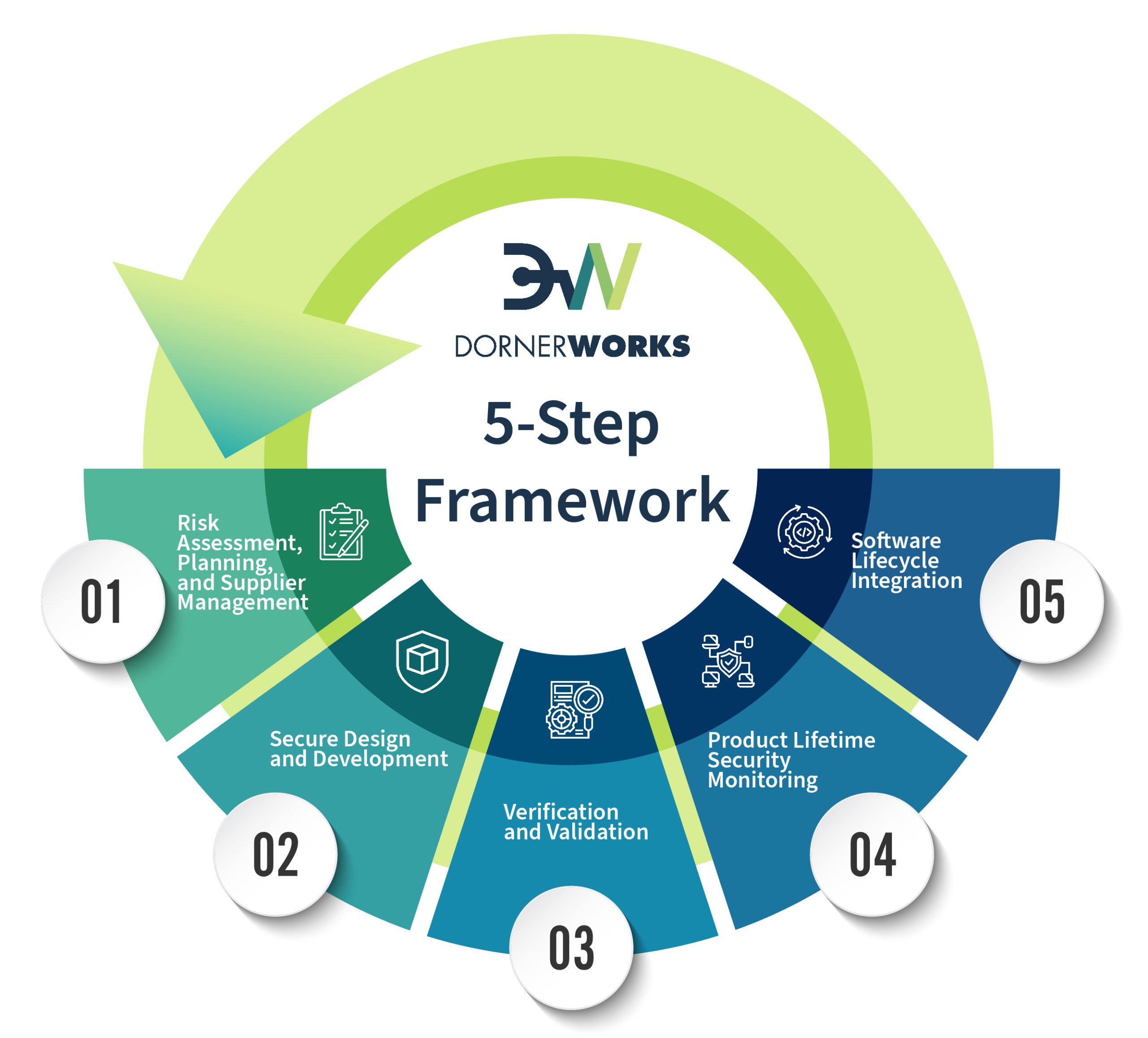
Risk Analysis: Identify potential risks related to data and IP security.
Strategic Planning: Develop a compliance strategy aligned with FDA regulations, including Incident Response!
Supplier Assessment: Evaluate suppliers for adherence to FDA requirements.
Design Controls: Implement FDA recommended design control practices.
Secure Development: Follow FDA guidance to create safe and effective software.
Testing: Conduct rigorous testing to verify device safety and performance.
Security Testing: Conduct static analysis and penetration testing against the device to verify resilience.
Post-Market Surveillance: Monitor device performance and user feedback post-launch.
Security Surveillance: Monitor SBOM content for new vulnerabilities. Patch regularly.
Adverse Event Reporting: Comply with FDA requirements for reporting adverse events.
Recalls and Corrections: Develop strategies for effective product recalls if necessary.
End of Life: Plan from Day 1 to protect data when your device is removed from service.
Software Changes: Manage software updates in the field while maintaining compliance.
Cybersecurity Updates: Regularly address and update device cybersecurity. Patch critical updates ASAP.
Documentation: Maintain accurate and updated records for FDA inspections.
Protect your data and stay one step ahead of cyber threats with DornerWorks’ robust cybersecurity solutions. Schedule a meeting with us today to fortify your organization’s defenses.
Sign up for updates on the latest cybersecurity news that impacts product developers. Submit the short form below and we will send you valuable cybersecurity resources to your inbox each quarter. Sign up now and stay in the know!